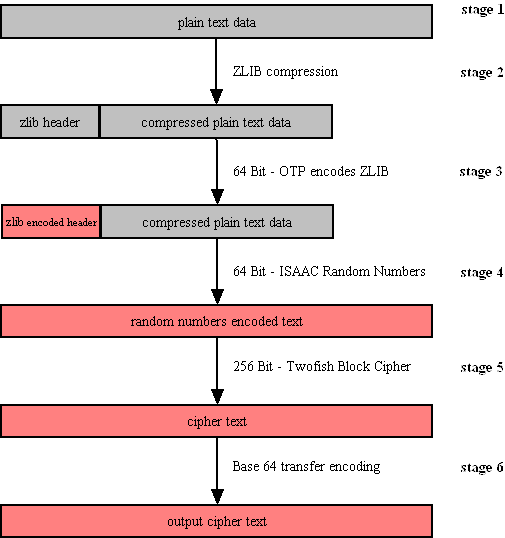
SecExMail encryption uses the Twofish block cipher in conjunction with the ISAAC random number generator and is optimized to operate on real-time email streams. It uses cryptographic primitives which are available to the general public and have been subject to extensive peer review. SecExMail encryption incorporates RSA public key encryption. Message encryption is performed via the Twofish block cipher and the ISAAC random number generator. SecExMail is warranted to be free from spy-ware, key escrow or key recovery features of any kind. The email encryption process is described in detail below. See diagram.
|
|
| 
|
| Email data is received in variable length data blocks. SecExMail parses SMTP header info, mail and data bodies.
|
| Because email messages frequently contain known plain text, such as salutation and or tag lines, which gives rise to known plain text attacks on the encrypted message and in order to minimize overall message expansion, the plain text is first compressed using the ZLIB compression algorithm. The net effect of deflating large amounts of data, containing both tidbits of known plain text such as greeting or tag lines as well as unknown message text into a compressed data stream is that any known plain text is effectively obscured.
|
| The ZLIB stream has a fixed header format which in itself might be exploited as known plain text by a savvy cryptanalyst. For this reason, the first 64 bits of the steam are encoded by way of a One Time Pad, using standard XOR masking. This approach acknowledges that email messages will contain portions of known plain text and proactively manages this problem.
|
| At this point the compressed data is XOR'ed using the 64 bit ISAAC random number stream.
|
| The next step in the encryption process is to encrypt the random number encoded text using the 256 bit Twofish block cipher. Twofish is used in chained block mode. Instead of XOR'ing the previous block's cipher text into the plain text of the current block, the output from the ISAAC layer is "chained in". This chaining process is illustrated below.
|
The final step is to assemble the output in base64 transfer encoded format for transmission via mail transfer agents (MTA).
|
|