Crypto Anywhere - Secure Email Utility Protecting Your Right to Privacy
This page is an unformatted version of the Crypto Anywhere product pages provided for easy searching. If you would like to view the formatted version, with index, please click here or on the link above.
Product: Crypto Anywhere
Operating Systems: Windows 2000, windows NT, Windows XP, Windows 98,
ME.
Category: Email and Network Security
Keywords: secure email,
privacy, internet privacy, pc privacy, secure e-mail, encryption
software, corporate email encryption,
corporate e-mail encryption, corporate email security, corporate e-mail security,
email security, email encryption,
e-mail security, e-mail encryption, email, e-mail, security, secure, confidential,
symmetric, encrypt, encrypting, encryption, online encryption, crypto, software,
free software, program, download, cryptography, privacy, communication, ecommerce,
pgp, aes, des, rsa.
Introduction
What is Crypto Anywhere ?
Crypto Anywhere is secure email on the move ! Crypto Anywhere is small enough to fit on a single floppy or USB key chain drive and so easy to use your grandma will be using it. Don't have a computer yourself but want to protect your web based e-mail at your local internet cafe ? Crypto Anywhere is for you ! If you suspect your employer is reading your private email, put an end to that. If you run Crypto Anywhere from a floppy disk or USB drive, you can encrypt your email without even installing software on your workstation. With Crypto Anywhere you can send and receive secure mail to and from anyone with an email account - the recipients do not have to be "crypto savvy" or even have Crypto Anywhere themselves.
Crypto Anywhere implements trusted, industry standard, strong encryption algorithms based on RSA public key encryption, the Twofish block cipher and the ISAAC random number generator. Crypto Anywhere e-mail is compatible with SecExMail client based and SecExMail Gate server based encryption. See SecExMail encryption.
Encrypting mail 1,2,3
Decrypting mail 1,2,3
For your eyes only
Preferences
Portable media
RSA Public Key Encryption
Crypto Anywhere / SecExMail Encryption
ISAAC Random Number Generator
SecExMail Message Format
One-Time Pads
Crypto Anywhere / SecExMail Keys
About Crypto Anywhere
About Bytefusion Ltd.
Acknowledgements
Working with Crypto Anywhere
Encrypting Mail 1,2,3
To encrypt mail, open Crypto Anywhere, select My Messages on the left, then click the Encryptor icon.
Step 1: Specify the recipient(s)
To specify the recipient of your message, click the "To:" button. This will display the For your eyes only screen. Crypto Anywhere automatically collects encryption keys from other people running Crypto Anywhere as you communicate them. If an encryption key is shown for the person or persons you wish to send e-mail to, select their name with your mouse and click "Ok". Otherwise, simply select "unlisted e-mail address" and provide both the email address and a passphrase for your message.
Step 2: Enter your message
If you are a registered user of Crypto Anywhere you may attach documents and files to your message.
Step 3: Encrypt the message
Select "Encipher" from the menu or click the encipher button. This will display the encrypted message or cryptogram, ready for sending. Click "Send".
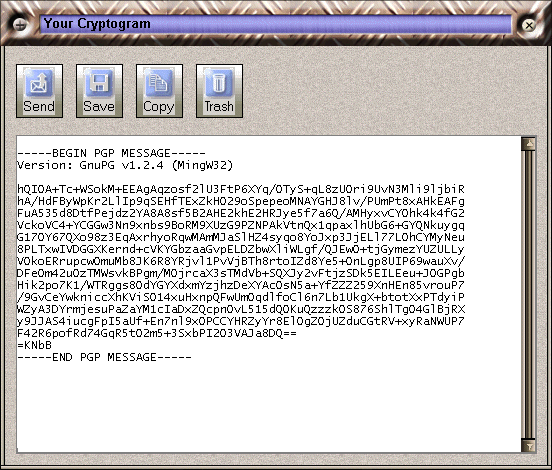
Decrypting Mail 1,2,3
If you have received a Crypto Anywhere message or cryptogram, follow the simple steps outlined below.
Step 1: Copy the encrypted message to the Windows clipboard
In your favorite e-mail client or web browser, select the entire encrypted e-mail with your mouse and copy it to the windows clipboard. To do this click above or to the left of the line
--Begin SecEx 1.1--
and hold the left mouse button down while scrolling to the end of the page. The entire message should now be highlighted. Now select Edit, Copy from the menu or use the keyboard shortcut Ctrl-C. This will copy the encrypted message to the Windows clipboard.
Step 2: Paste the encrypted message into Crypto Anywhere
Open Crypto Anywhere. Select My Messages on the left, then click the Decryptor icon. Now click the Paste button on the toolbar.
Step 3: Decrypt the message
Select "Decipher" from the Crypto Anywhere menu or click the decipher button on the toolbar. This will decrypt the message and display the plain text in the message window.
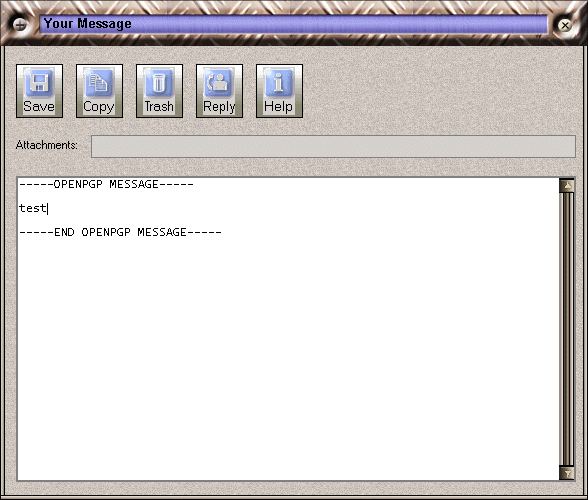
For your eyes only screen
When sending encrypted e-mail, you will need to specify the recipient(s) of your message. As you receive Crypto Anywhere messages from other people, Crypto Anywhere collects encryption keys from the senders - your secure friends. When sending mail to your secure friends, messages are encrypted so that only your secure friends will be able to read them. You yourself won't be able to decrypt a message encrypted to a secure friend - unless of course you selected your own key for encryption also. You may select one or more keys. Using secure friend keys is the recommended mode of encryption.

In many cases, the intended recipient of a message has not provided you with an encryption key. This will be especially the case when communicating with someone for the first time. In this case simply click "unlisted email address". This will select "Self decrypting e-mail" as encryption method.
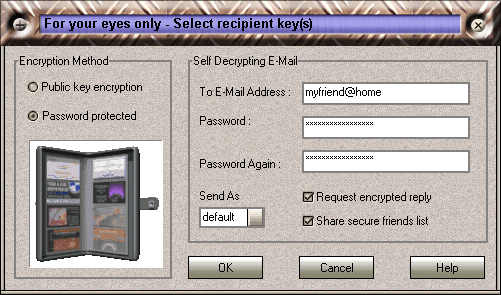
Self decrypting e-mail messages carry an attachment which bundles your encrypted message, the Crypto Anywhere software needed to decrypt the message and any required encryption keys into a self extracting archive. The encryption key required to decode the message is itself stored using 3DES encryption and protected by the passphrase you supply. Therefore you will need to supply the recipient of the message with this passphrase. The ability to receive email ments will vary from recipient to recipient. Some email clients or email servers block self extracting attachments or block attachments with specific file names or extensions. For this reason you may send self decrypting e-mails in three formats under "Send As". The following options are supported :
Request encrypted reply
Check this option if you want to include keys needed to send you encrypted e-mail ( your public keys ).
Share secure friends list
Check this option if you want to share your secure friends list with the recipients ( secure friends public keys ).
In most cases you will only have to send a self decrypting email to a particular recipient once. After decrypting and reading your message, the recipient will be given the option to configure CryptoAnywhere immediately and send you encrypted mail in reply.
Preferences
The preferences window allows you to customize the behavior of Crypto Anywhere.
MAPI compliant email client :
MAPI is an acronym for messaging application programming interface and allows Windows applications to use existing e-mail accounts without further configuration. E-Mail clients which support MAPI include Microsoft Outlook and Eudora. Use this option if you have a MAPI compatible e-mail client and intend to use Crypto Anywhere mostly on your own computer. If you are storing Crypto Anywhere on a floppy or other portable medium for use on different computers, the SMTP module is the recommended option. If you are unsure if your computer supports MAPI, you may test for MAPI compatibility via the configuration wizard.
Built in SMTP component :
Crypto Anywhere has a built in SMTP module to send e-mail. This allows Crypto Anywhere to send e-mail independently of mail settings of the computer or computers on which it is run. This option is especially useful if you plan to use Crypto Anywhere in internet cafe's. Some service providers do not allow access to their SMTP send mail servers when connecting from other service provider's networks and might require SMTP logon to permit you to send mail. See "Server requires user authentication".
Server :
This option is only required in SMTP mode. Please provide the DNS name or IP address of your outgoing mail server.
Port :
This option is only required in SMTP mode. Please provide the port number of your outgoing mail server SMTP service. It is safe to leave the default value.
Server requires user authentication :
This option is only required in SMTP mode. Some service providers require user logon to permit sending of e-mail. Usually this is the same information as is required for the checking of e-mail. User logon, also called SMTP AUTH, is only available with extended SMTP, or ESMTP.
User :
This option is only required in extended SMTP mode with SMTP AUTH. Please enter your user name for your e-mail account.
Password :
This option is only required in extended SMTP mode with SMTP AUTH. Please enter your password for your e-mail account.
Your e-mail address :
This option specifies your return e-mail address or "reply-to" address. By default, the "reply-to" e-mail address corresponds to the e-mail address of your default Crypto Anywhere / SecExMail key.
Append my public key to end of e-mails :
If you check this option, Crypto Anywhere will append your default public key to the end of outgoing messages as a "tag line". This enables other users to send encrypted mail to you. You will be added to the secure friends list of other Crypto Anywhere users automatically
Accept auto update of public keys :
If you check this option, Crypto Anywhere will accept new public keys from other people and add them to your secure friends list when ever a key is not found on your secure friends list already. You will be prompted prior to each update.
Microsoft and Eudora are trademarks or registered trademarks of their respective owners.
Portable Media
If you have installed Crypto Anywhere on your hard drive ( typically c:\cryptoanywhere ) and wish to use it on a floppy drive, USB drive or similar removable medium, simply copy the entire CryptoAnywhere installation folder to your removable medium.
Files you need to copy:
|
File |
Comment |
|
cryptoanywhere.exe |
main executable |
|
cryptoanywhere.hlp |
help file |
|
cryptoanywhere.cnt |
help file index |
|
crypto.conf |
configuration file |
|
secexmail.rnd |
random number generator seed |
|
*.pubrsa |
public key files |
|
*.privrsa |
private key files |
Approximate space requirement 1 MB.
Technical
RSA Public Key Encryption
|
"c = me mod n" is the algorithm that turns the world of e-commerce. Introduced in 1978 by Rivest, Shamir and Adleman after whom the cipher is named, RSA is the worlds foremost public key encryption system. Contrary to the design of classic encryption algorithms where the same key is used to lock and unlock the information, public key encryption relies on "two key" algorithms. The sender encrypts the message with the recipients public key who, upon receipt of the message, is able to decipher the same with the private key counterpart. This development was revolutionary in the field of cryptography because parties wishing to establish secure communications no longer had to meet in "secret" to exchange confidential keying information. The SecExMail public key infrastructure uses industry standard RSA encryption as developed by the OpenSSL project. See Acknowledgements. |
|
Crypto Anywhere / SecExMail Encryption
|
SecExMail encryption uses the Twofish block cipher in conjunction with the ISAAC random number generator and is optimized to operate on real-time email streams. It uses cryptographic primitives which are available to the general public and have been subject to extensive peer review. SecExMail encryption incorporates RSA public key encryption. Message encryption is performed via the Twofish block cipher and the ISAAC random number generator. SecExMail is warranted to be free from spy-ware, key escrow or key recovery features of any kind. The email encryption process is described in detail below. See diagram. |
|
SecExMail Encryption
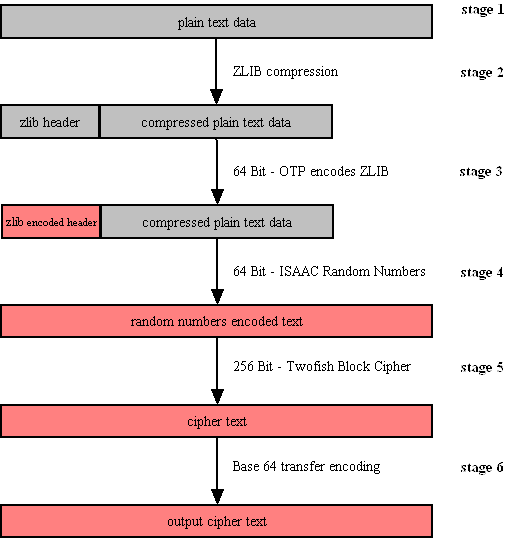
Email data is received in variable length data blocks. SecExMail parses SMTP header info, mail and data bodies.
Because email messages frequently contain known plain text, such as salutation and or tag lines, which gives rise to known plain text attacks on the encrypted message and in order to minimize overall message expansion, the plain text is first compressed using the ZLIB compression algorithm. The net effect of deflating large amounts of data, containing both tidbits of known plain text such as greeting or tag lines as well as unknown message text into a compressed data stream is that any known plain text is effectively obscured.
The ZLIB stream has a fixed header format which in itself might be exploited as known plain text by a savvy cryptanalyst. For this reason, the first 64 bits of the steam are encoded by way of a One Time Pad, using standard XOR masking. This approach acknowledges that email messages will contain portions of known plain text and proactively manages this problem.
At this point the compressed data is XOR'ed using the 64 bit ISAAC random number stream.
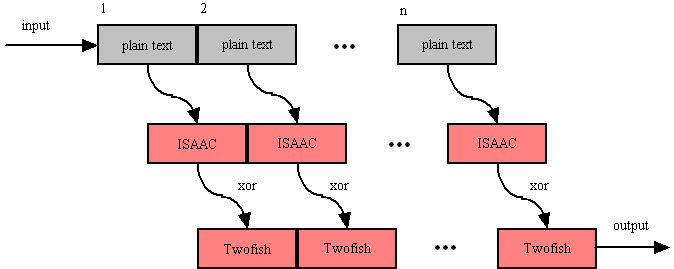
The next step in the encryption process is to encrypt the random number encoded text using the 256 bit Twofish block cipher. Twofish is used in chained block mode. Instead of XOR'ing the previous block's cipher text into the plain text of the current block, the output from the ISAAC layer is "chained in". This chaining process is illustrated below.
Twofish Block Chaining
The final step is to assemble the output in base64 transfer encoded format for transmission via mail transfer agents (MTA).
ISAAC Random Number Generator
|
ISAAC (Indirection, Shift, Accumulate, Add, and Count) is a cryptographically secure pseudo random number generator. With an average cycle length of 2 to the 8295th power its output is uniformly distributed and unpredictable. ISAAC has been developed by Bob Jenkins and placed into the public domain in 1996. See Acknowledgements for legal information on ISAAC. ISAAC is at the heart of SecExMail's entropy collection system. |
|
SecExMail Message Format
SecExMail messages are transferred in base64 encoded format. Messages may be encrypted to multiple recipients. The internal message layout is defined as follows :
[<rsa bytes>:<recipient>]key[<rsa bytes>:<recipient>]key...cipher text
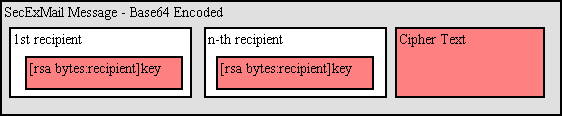
This is the size of the recipient's RSA key in bytes. Therefore a 2048 bit RSA key would be listed
as having a size of 256 bytes. RSA This parameter is defined for RSA key sizes of 2048, 4096, and 8192 bits.
This is the email address of the recipient to whom the message is encoded.
This is the SecExMail session key material, encrypted with the RSA public key of the recipient.
The SecExMail session key is used to encrypt the message body of the email message and is comprised
of a 64 bit One Time Pad key, a 64 bit ISAAC random number generator key, and a 256 bit Twofish key.
This is the message body encrypted using SecExMail Encryption.
A typical SecExMail message is depicted below :
--Begin SecEx 1.1--
WzI1NjpjaHJpc0BvZmZzaG9yZW1haWxyb29tLmNvbV0dJyyJnwwCm0LI0659zpBY/asERA3FRG99
OYRhm5f+rwohYORt8Wp3rmwI2Nguhk38KvH5pg8ZRTXXWiEHYMakQPPXpbnaJepJFZeXTcNMTi/d
p0Rc5HCTui5okW/00Gv8Sp328Ldh3DlgQcGW7oYt9qxG/cJ/PaVxxxEfDM3I4cnsCyLjfX+I0JY6
h+emWt4U/N6u+K0tPL4ua2OfGhGoBXo+6KK042bXGpk/Pj6WEOQMcKyR+VrsOx6ZcTgpqS3WCcUc
2/JDy9zHqlkPLohXcT4G2Hiwp/1JhviaQtoKA2NYYimuY5ZjNUGPMsIaN0h6AKS3/qZsHhK1LtcA
WpLnuoFbQleekuJngBCC1RIlIlI4lfFgMkxoUkZrtXg6E217Q6GMMhHMANJ4EU3D2c1BgauDYAQG
Rpz0p8efm/WAZoXai6KVElMEiK7tv98s8wu9LpUxN44QYj2eNRVI+72lGPfkBoKvr6eK5/TU4cHN
Dg9VxCGj4n8KDvfYsPRpBSNzLL+Ta4iz7toQ/MGdPCQa
--End SecEx Mail--
One-Time Pads
|
A one-time pad is a block of random data used to encrypt a block of equal length plain text data. Encryption is usually by way of XOR'ing the one-time pad with the message text. This process may be thought of as a 100% noise source used to mask the message. The one-time pad is secure if it is comprised of random data and is never reused. Because of this, one-time pads have limited application in modern ciphers, but are commonly acknowledged as the holy grail of cryptography. SecExMail uses one-time pads to encrypt the ZLIB compression header in SecExMail messages.
|
|
Crypto Anywhere / SecExMail Keys
|
SecExMail employs public key encryption. Messages are encrypted to one or more recipients using their public keys. Only the intended recipient can, upon receipt of the message, recover the plain text using his/her private key. Public key encryption differs from classical encryption because the recipient of a message does not use the same key for decryption as the sender used for encryption. In cryptography the fictional characters "Alice" and "Bob" are often used for illustration purposes. Consider the following scenario : Alice lives in New York and Bob lives in Los Angeles. Alice wants Bob to be able to send her confidential mail. She goes to her local hardware store and purchases a dozen or so combination padlocks, sets the unlocking code on each padlock, confuses the dials again, and sends the open padlocks to Bob in Los Angeles. |
|
Bob is now in possession of Alice's padlocks, but not the unlocking codes. When Bob wants to send Alice a confidential letter, he places the letter inside a steel box and locks it with one of Alice's padlocks. Once the padlock is snapped shut, even he himself cannot re-open the box since he is not in possession of the combination which will release the lock. Only Alice will be able to open the box and therefore read the letter once she has received Bob's parcel in the mail.
Public key encryption works much in the same manner. The public key may be thought of as an open, electronic padlock. You can send this electronic padlock to all your friends. Your friends may then use that padlock to secure their emails to you in an electronic box. This electronic box is the encrypted email. Upon receipt of the encrypted email, you dial the secret combination which is your private key and retrieve the original message.
SecExMail does all this for you.
About
About Crypto Anywhere

Crypto Anywhere
Version 1.1
Copyright © 2003, Bytefusion Ltd.
All Rights Reserved
About Bytefusion Ltd.

Bytefusion Ltd.
22 Duke Street
Douglas, IOM
IM1 2AY
British Isles
Inquiries: sales@bytefusion.com
Acknowledgements
At the time of writing, the ISAAC home page can be found at http://burtleburtle.net/bob/rand/isaacafa.html.
ISAAC has been placed into the public domain by its author, Bob Jenkins in 1996.
-----------------------------------------------------------------------------------------------------------
My random number generator, ISAAC.
(c) Bob Jenkins, March 1996, Public Domain
You may use this code in any way you wish, and it is free. No warrantee.
-----------------------------------------------------------------------------------------------------------
The RSA algorithm was patented until September 2000 when RSA® Security Inc. released the algorithm into the public domain. "BEDFORD, Mass., September 6, 2000 -- RSA® Security Inc. (NASDAQ: RSAS) today announced it has released the RSA public key encryption algorithm into the public domain, allowing anyone to create products that incorporate their own implementation of the algorithm."At the time of writing a copy of this statement can be found at http://www.rsasecurity.com/news/pr/000906-1.html
The Twofish block cipher by Counterpane Labs was developed and analyzed by Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall and Niels Ferguson. Twofish was one of the five Advanced Encryption Standard finalists. At the time of writing the Twofish homepage can be found at http://www.counterpane.com/twofish.html. The cipher has been made available to the general public by the following statement on http://www.counterpane.com/about-twofish.html :
" Twofish is unpatented, and the source code is uncopyrighted and license-free; it is free for all uses. Everyone is welcome to download Twofish and use it in their application. There are no rules about use, although I would appreciate being notified of any commercial applications using the algorithm so that I can list them on this website. "
ZLIB is a lossless data-compression library written by Jean-loup Gailly and Mark Adler. ZLIB is made
available as free, unpatented software to the general public at http://www.gzip.org/zlib/. The license
conditions are set forth at http://www.gzip.org/zlib/zlib_license.html and reproduced below :
" Copyright (C) 1995-2002 Jean-loup Gailly and Mark Adler
This software is provided 'as-is', without any express or implied
warranty. In no event will the authors be held liable for any damages
arising from the use of this software.
Permission is granted to anyone to use this software for any purpose,
including commercial applications, and to alter it and redistribute it
freely, subject to the following restrictions:
1. The origin of this software must not be misrepresented; you must not
claim that you wrote the original software. If you use this software
in a product, an acknowledgment in the product documentation would be
appreciated but is not required.
2. Altered source versions must be plainly marked as such, and must not be
misrepresented as being the original software.
3. This notice may not be removed or altered from any source distribution.
Jean-loup Gailly jloup@gzip.org
Mark Adler madler@alumni.caltech.edu "
The RIPE message digest was written by Antoon Bosselaers for Katholieke Universiteit Leuven, Department of Electrical Engineering ESAT/COSIC, Belgium. License conditions ask us to quote the following :
" RIPEMD-160 software written by Antoon Bosselaers,
available at http://www.esat.kuleuven.ac.be/~cosicart/ps/AB-9601/ "
Katja Bengtsson of Brisbane, Australia ( katja@offshoremailroom.com )
SecExMail contains cryptographic software from the OpenSSL project at www.openssl.org which is licensed under a "BSD-style" open source licenses. These licenses asks us to state the following :
"This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
"This product includes cryptographic software written by Eric Young (eay@cryptsoft.com). This product includes software written by Tim Hudson (tjh@cryptsoft.com)."
SecExMail is an independent, derived work and no endorsement of SecExMail by the OpenSSL project is implied. The full text of the OpenSSL license and the original SSLeay License is reproduced below.
OpenSSL License
====================================================================
Copyright (c) 1998-2001 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this
software must display the following acknowledgment:
"This product includes software developed by the OpenSSL Project
for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
endorse or promote products derived from this software without
prior written permission. For written permission, please contact
openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL"
nor may "OpenSSL" appear in their names without prior written
permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following
acknowledgment:
"This product includes software developed by the OpenSSL Project
for use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE POSSIBILITY OF SUCH DAMAGE.
====================================================================
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim
Hudson (tjh@cryptsoft.com).
Original SSLeay License
Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
All rights reserved.
This package is an SSL implementation written
by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as
the following conditions are adhered to. The following conditions
apply to all code found in this distribution, be it the RC4, RSA,
lhash, DES, etc., code; not just the SSL code. The SSL documentation
included with this distribution is covered by the same copyright terms
except that the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in
the code are not to be removed.
If this package is used in a product, Eric Young should be given attribution
as the author of the parts of the library used.
This can be in the form of a textual message at program startup or
in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement:
"This product includes cryptographic software written by
Eric Young (eay@cryptsoft.com)"
The word 'cryptographic' can be left out if the routines from the library
being used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from
the apps directory (application code) you must include an acknowledgement:
"This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
The licence and distribution terms for any publicly available version or
derivative of this code cannot be changed. i.e. this code cannot simply be
copied and put under another distribution licence
[including the GNU Public Licence.]
Chris Kohlhepp and Mark Robertson, Bytefusion Ltd.
Your index page goes here...
In MS-Word, select INDEX AND CONTENTS from the INSERT menu.
Select INDEX and click OK.